5Charlie CTF - Myste-RE
A write-up of the “Myste-RE” reverse-engineering challenge from 5Charlie CTF.
Myste-RE 1
Myste-RE 1 - Challenge
Somebody made this to do something, but what?
Note: Flag format is flag(*).
Attachments: flag - Binary
Myste-RE 1 - Solution
This one took a hot minute to figure out.
Our team played around with various architectures and eventually agreed that 16-bit x86 made the most sense.
We were able to create environment and read through using radare2 and the commands e asm.arch=x86 and e asm.bits=16.
We had some trouble getting an environment running but eventually decided to package it up as a DOSBox package and upload it to an online javascript-based DOSBox emulator: https://caiiiycuk.github.io/dosify/
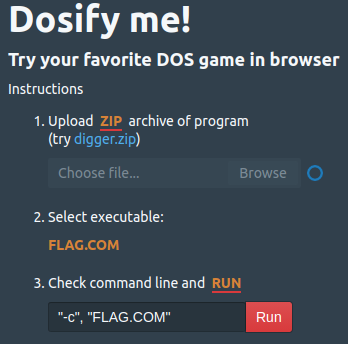
We give it a run…
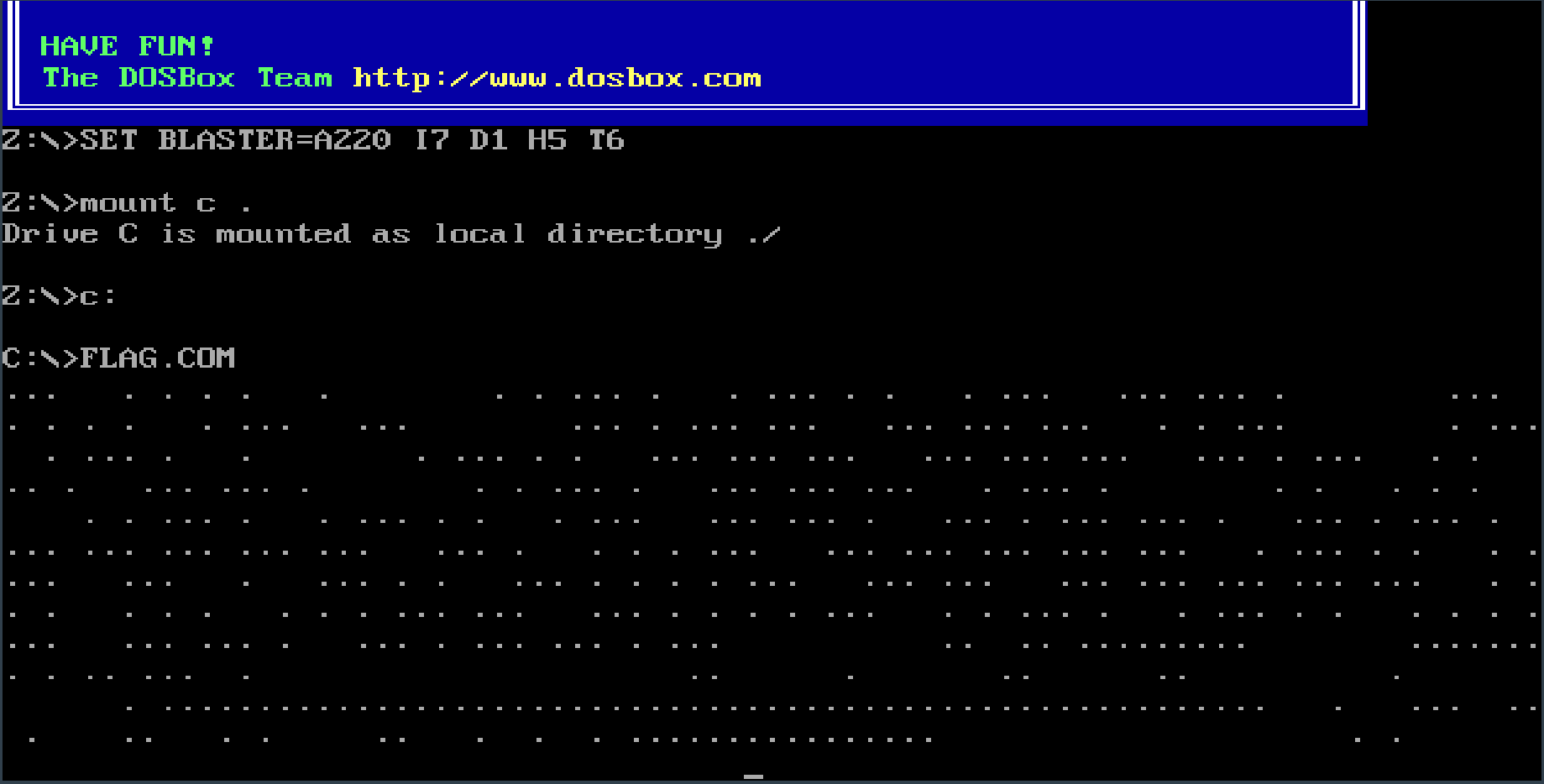
Now we start seeing a bunch of dots being printed to the screen. It turns out that triple-dots are dashes, the single dots are dots, and the long breaks are character delimiters- morse code! And then I copied that by hand into CyberChef.
Flag: FLAG(C0NV0LUTED-M0RS3-FL4G)
Whoever made this enjoys suffering.
