5Charlie CTF - Covert Channel - Normal
A write-up of the “Normal” network covert-channel pcap analysis challenge from 5Charlie CTF.
Normal
Normal - Challenge
Just some normal traffic. Can you find a flag?
Attachments: normal.pcapng
Normal - Solution
Taking a look at the pcap most things look normal at a glance with one exception. There are intermittent TCP SYNs to port 8000 sprinkled in. We can confirm the funky traffic by looking at the TCP conversations in Wireshark, sorted by destination port.
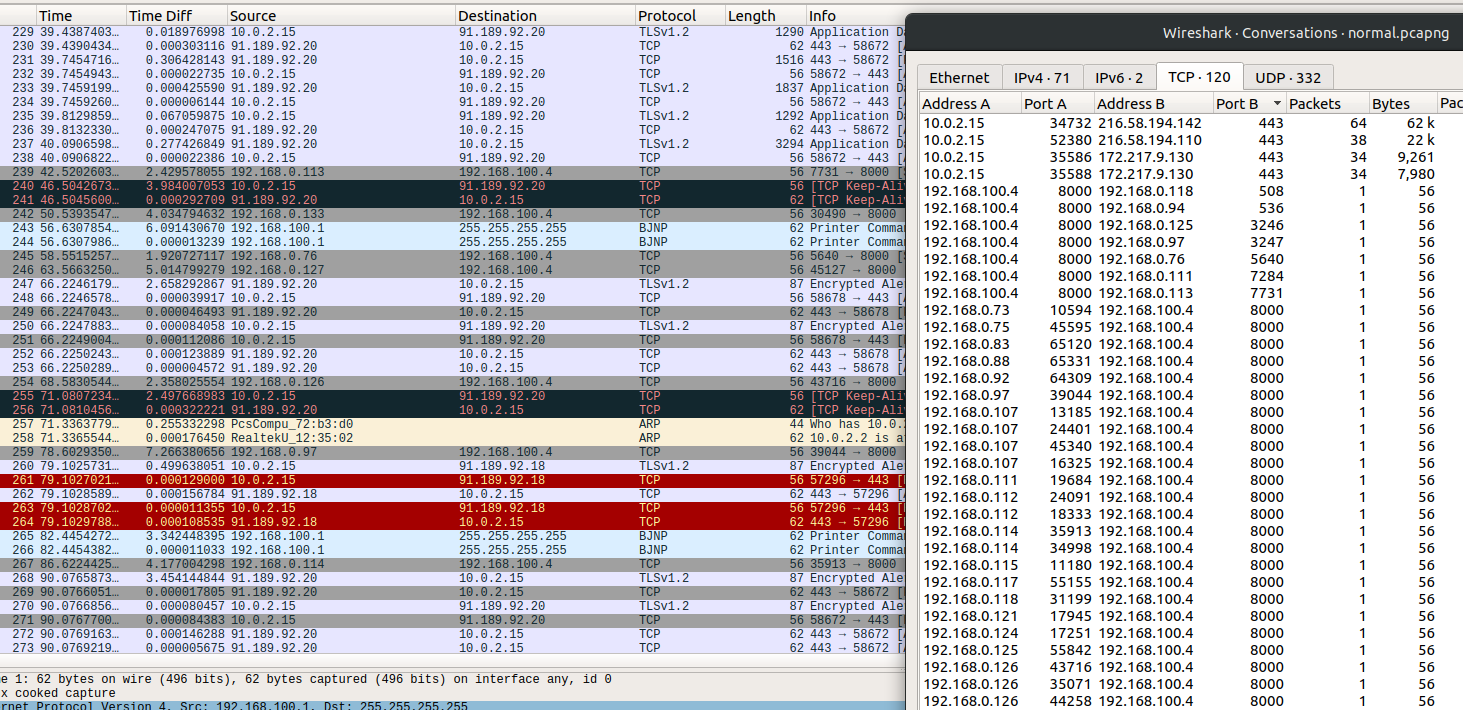
Filtering on our suspicious traffic, we notice that the source address changes with each request.
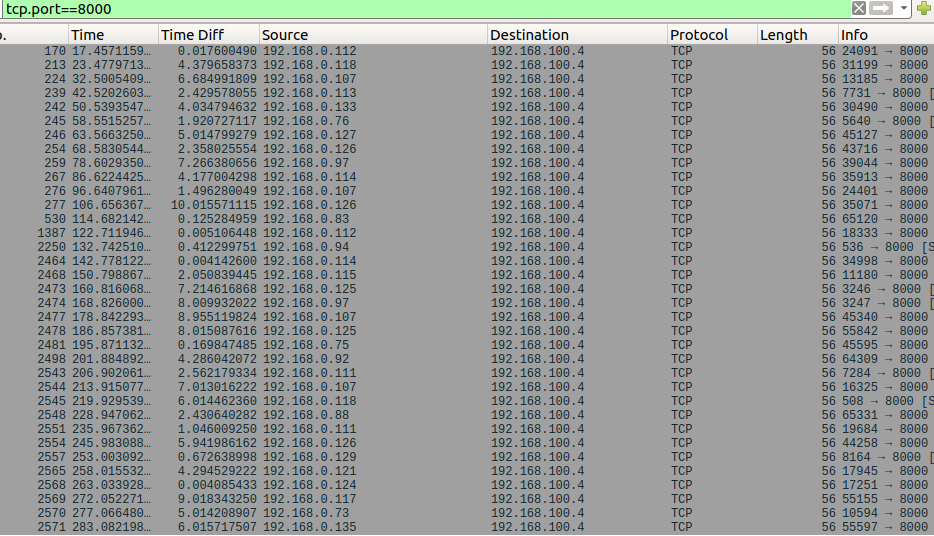
If you’re familiar with how flags look in different formats, you may recognize that the offsets between the source addresses look similar to the offsets between the ordinal value of “flag”. It’s not an exact match though… each value is incremented by 10.
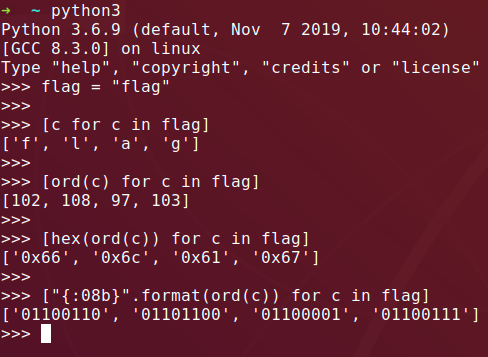
Let’s use tshark and a little scripting to pull all the data out of the last octet of each matching packet, decrementing the value returned for each by 10.
tshark -r normal.pcapng -Y "tcp.dstport==8000" -T fields -e ip.src_host \
| python3 -c \
"import sys;
data = sys.stdin.read();
data = data.split();
[print(int(d.split('.')[-1])-10) for d in data]"Using the output we can use CyberChef to convert it using FromDecimal.
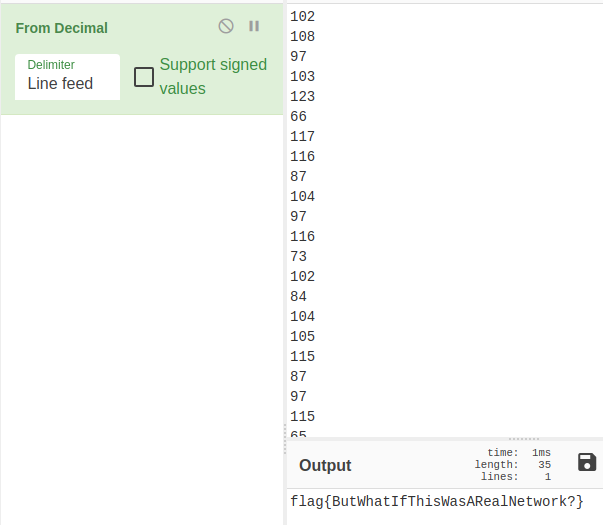
Integers go in, flag falls out. 😃
Flag: flag{ButWhatIfThisWasARealNetwork?}
